Just a few days after writing an article on how to avoid phishing and spoofing scams, it was with precision timing that we were the target of a phishing attempt on Twitter. Always grateful for extra blog material :)
A Twitter Phishing Expedition
The benefit of shortened links is they are short, the downside is they mask the destination website address, so are ideal for phishing scams. Visiting the page through the mobile Twitter app won't automatically show you the destination website address, so it's easy to understand why some people may be tricked into entering their details while on the move.
Spoofed website
The link takes you to what looks like the Twitter website, where you're told that your session has timed out and you need to enter your username and password to sign in.
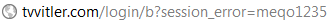
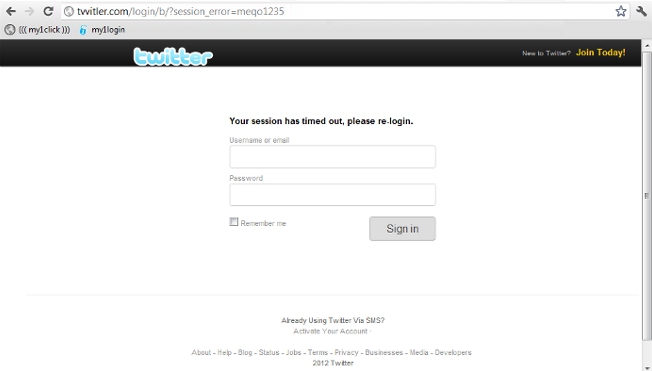 As discussed in our recent blog article, be wary of any site which asks you to fill in login details after clicking a link. At first glance the site may look okay, but take a closer look at the website address:
As discussed in our recent blog article, be wary of any site which asks you to fill in login details after clicking a link. At first glance the site may look okay, but take a closer look at the website address:
Anyone who enters their details into the fields and clicks 'Sign in' will have their username and password captured and then be forwarded and logged into the legitimate twitter.com site, so they may not be aware that it's happened. The account that sent us the message was most-likely an earlier victim of the scam.
What to do if you've been caught out and entered your details
You should visit the legitimate Twitter website immediately and if you can still access your account, change your password, and if you've used that same password on other sites you need to change it on those too. If you can't access your account visit the Twitter Compromised Accounts help page. You should also report the phishing site to Twitter.
It always pays to be suspicious of unsolicited messages or emails which ask you to sign into or verify accounts. Making yourself aware of phishing and spoofing methods will make these scams much more obvious to you and reduce the chances of ever being affected.
Further Reading