
Why Your Password Policy Is Broken

Every IT Department worth their salt has a password policy that their employees are required to adhere to. In reality though, your password policy is broken and it won't keep your company secure...
Why is your password policy broken? Because employees are only human; and will find the most-convenient way to adhere to the policy. They do this by creating passwords that meet the policy requirements, but that are weak and easy to guess.
Password Policies
Password requirements for internal applications and directories, where users are accessing corporate-owned systems, can be set by the organisation. However, employees also typically use a multitude of externally-hosted applications. For these apps, organisations are at the mercy of the password requirements set by those service providers, and can only offer guidance for their users as to how they should create passwords.
Password requirements typically comprise; a minimum length, a maximum length, passwords requiring specific characters (such as uppercase, lowercase, numbers or special characters), etc.
There can also be requirements as to the type of passwords employees can use, for example; old passwords cannot be re-used, lockout threshold (3 failed login attempts blocks the system), reset time after lockout (can’t reset password for 20 minutes after lockout), etc.
External target applications may ask for something like this (this is Salesforce).
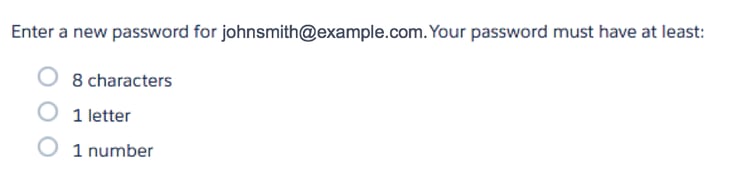
While the organisation has more control over password requirements for internal applications than external applications, in both instances, it is still down to the user to create and manage the passwords.
So, why don’t password policies and minimum password requirements work?
Why Password Policies Don't Work
The measures in place to determine password strength are outdated; these do not take into account the increased sophistication of the tools available to hackers or the fact that a password that meets the requirements doesn’t necessarily make it strong. For example, if you were to use ‘Password1’ for your work PC, while this may meet the requirements of one uppercase letter and one digit, it’s an extremely weak password as it is easy to guess, commonly used and will appear in password dictionaries.
Furthermore, it is human nature to focus on convenience over security. Staff will unconsciously choose passwords that are easily socially engineered, such as using family, pet or sports team names, and if they are required to regularly change an application password, they are likely to introduce patterns, such as incrementing a digit.
The 25 Most-Common Passwords
These might seem incredibly easy to guess or hack, but you’d be surprised how many people globally, use passwords just like these in their every day work lives. A sizeable number of your staff will be using passwords like these to protect your company accounts:
| 1. 123456 | 10. baseball | 19. letmein |
| 2. password | 11. welcome | 20. login |
| 3. 12345678 | 12. 1234567890 | 21. princess |
| 4. qwerty | 13. abc123 | 22. qwertyuiop |
| 5. 12345 | 14. 111111 | 23. solo |
| 6. 123456789 | 15. 1qaz2wsx | 24. passw0rd |
| 7. football | 16. dragon | 25. starwars |
| 8. 1234 | 17. master | |
| 9. 1234567 | 18. monkey |
If you suspect your employees are using any of these passwords, now might be a good time to run a password audit to find out, and then look to change these passwords to something more secure. If you’d like to test your password strength, try our Password Strength Calculator.
How to Regain Control Over Password Policies
So, what can you do to better-secure your organisation from a data breach due to weak passwords? Be smarter about access and authentication policies; accept that employees are your weakest link and that changing their behaviour is next to impossible. You can effectively save employees from themselves by making some changes that don’t require them to change the way they work. This can come in a number of forms:
- Remove the need for passwords – where possible, organisations can replace credential-based authentication with token-based authentication (e.g. SAML) by implementing Single Sign-On (SSO).
- Auto-generate passwords – for applications where removing password authentication is not possible, organisations can implement SSO that will auto-generate strong passwords on users’ behalf. This eliminates the vulnerabilities introduced by employees, ensuring passwords are long, strong and unique. Additionally, the SSO auto-fills these credentials when users need to sign into their applications, so employees don’t need to actually remember these complex passwords – a significant usability improvement for employees.
- Mnemonic Password Practices – in situations where users would still need to remember passwords, e.g. Active Directory, it’s important to educate employees on how they can make passwords stronger, but also easier to remember. One such technique is using mnemonics to create a unique password which is all but impossible to crack, e.g. taking the first letter from each word of a sentence such as "My best friend just bought a new iPad which is really great” and adding some entropy would create the password MbFjB&nIpw1rG!. This will still require memory, but remembering a structured sentence and applying it as a password is easier than remembering a random collection of letters, numbers and symbols. The resulting password MbFjB&nIpw1rG! would take a supercomputer around 500 billion years to crack.
What Does the Future Hold?
If there’s one thing you should take away from this article, it’s that having a password policy in place does not solve the problem of weak passwords. Weak passwords are still in use throughout your organisation, from top to bottom.
Nobody can predict that your organisation will definitely suffer a data breach due to inneffective password policies, but let's look at the stats:
- 90% of large organisations suffered a security breach last year*
- 65% of data breaches are caused by weak password practices by employees**
- £2.3m is the average cost of a data breach to a large UK organisation*
The question to ask yourself is, what odds would the bookmakers give you on avoiding a data breach?
If you think your organisation could benefit from an Single Sign-On solution, why not read our White Paper; TEN Signs You Need SSO.
* Source: HM Government Information Security Breaches Survey 2015
** Source: Verizon Data Breach Report
Related Articles
Why Corporate Password Policies Don't Work Against Hacks
It’s no secret that passwords pose a significant problem for organisations. The oldest and most common form of digital authentication is also the least secure, with...Why are we still using passwords in 2022?
With Verizon reporting that 82% of data breaches involved the Human Element, why are businesses still using passwords and putting their security and reputation in...Identity and Access Management for Web, Mobile and Windows Desktop Applications
Identity and Access Management for Web, Mobile and Windows Desktop Applications










-
© My1Login 2007 - 2025
- Terms & Conditions
- Anti-Slavery Policy
- Back to the top ↑

