Secure Workforce Access to Corporate Applications
Protect high-value and sensitive accounts by activating step-up and MFA policies before releasing credentials or SSO rights for specific applications.
-
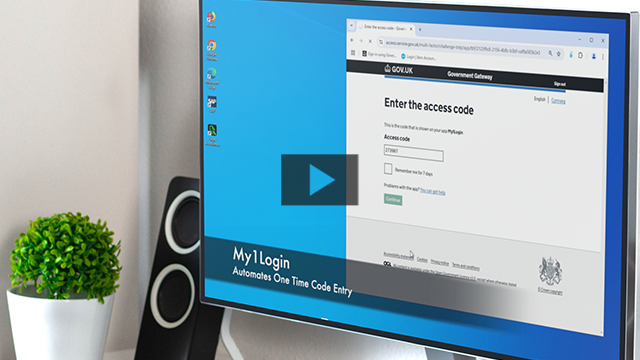
 Auto-Fill One Time Passwords
Auto-Fill One Time Passwords
-
 App and User Specific Step-Up and MFA Policies
App and User Specific Step-Up and MFA Policies
-
 Leverage Mobile Biometrics
Leverage Mobile Biometrics
-
 Integrate Authenticator Apps
Integrate Authenticator Apps
-
 Integrate Authenticator Tokens
Integrate Authenticator Tokens
One Time Passwords
My1Login can be configured to automatically fill one-time passwords when the user is prompted for these. This, in conjunction with Single Sign-On (SSO), enables automation of the entire login process.
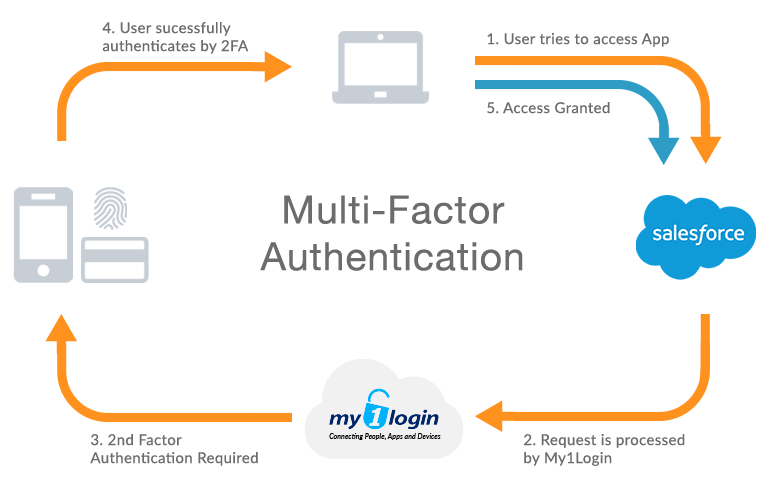
My1Login can also integrate with numerous third-party, multi-factor methods to protect access to My1Login and to protect access to specific credentials stored within My1Login.

Flexible User Policy Framework
Secure company data without compromising user productivity. Configure application-specific policies that invoke step-up and MFA challenges. Users need to satisfy these challenges before credentials or SSO access to specific, high-value accounts and services is made available to them.
-
User
-
Group
-
Application
-
On Prem / Off Prem
-
IP Location
Integrate the latest authentication methods with your My1Login account to control elevated user access privileges.
Local Biometrics
The embedded technology in mobile devices and existing authenticator apps can provide a second-factor authentication alternative. Whether this is by: touch pattern; thumbprint; audio; facial recognition; voice or audio, local biometrics harness the power of the mobiles already in the hands of your users to assure identity.

RFID, Hardware and Public Key Tokens
Where hardware tokens and smartcards are used for access to the network, My1Login can compliment this by leveraging delegated trust and using it to onward authenticate users with downstream, internal and external applications.